In the game of rugby, after an infringement or out-of-play ball, both
teams engage in a formation called Scrum (short for scrummage) in order to
compete for possession. The nature of the play is quite dangerous and has
resulted in injuries and a couple of deaths.
The type of scrum focused on in this
article is, fortunately, not life threatening.
In American football, the coach calls
each play prior to its implementation by the players - a play that has been
practiced and drilled before the game so that each player knows exactly where
to go and what his role is. After that play is over, the coach will call
another. This process works by using a "defined steps" approach.
In rugby, however, plays don't usually
work out as planned and become chaotic and frenzied. Predefined steps in the
play will be abandoned, because they do not work in the random nature of the
sport. Instead, the rugby coach must teach his players how to be spontaneous,
self-organizing, and able to act on the fly. The coach will teach basic rugby
patterns that the team will adjust as needed when in action, while making
periodic assessments of the patterns and changing them based on success or
failure.
The scrum approach to IT project management works in a similar manner to
the way a rugby coach organizes his plays. The customer, or product owner,
provides a set of objectives he or she desires to reach. The project manager,
or ScrumMaster, will create a self-organizing team, but give them no specific
steps for achieving the objective(s)2. This allows the
team to decide what to do and how to do it as they encounter surprises,
problems, or difficulties. At the end of each iteration, or Sprint, of the
project, the team presents its work, allowing the product owner to assess
what's been done and make changes to the requirements, priorities, and release
plans. At the same time, the scrummaster coaches the team as they adapt their
project plans and processes.
Roles
Just as a rugby team has various players in different positions (like
Fly-Half, Number 8, and Prop), so too does the scrum process team3. According to the Scrum Alliance, there are three:
The Team
- ·
Is cross-functional, with seven (plus or minus two) members
- ·
Selects the sprint goal and specifies work results
- ·
Has the right to do everything within the boundaries of the project
guidelines to reach the sprint goal
- ·
Organizes itself and its work
- ·
Demos work results to the product owner
The Product Owner
- ·
Defines the features of the product
- ·
Decides on release date and content
- ·
Is responsible for the profitability of the product (ROI)
- ·
Prioritizes features according to market value
- ·
Adjusts features and priority every 30 days, or as needed
- ·
Accepts or rejects work results
The ScrumMaster
- ·
Ensures that the team is fully functional and productive
- ·
Enables close cooperation across all roles and functions
- ·
Removes barriers
- ·
Shields the team from external interferences
- ·
Ensures that the process is followed, including issuing invitations to
Daily Scrum, Sprint Review, and Sprint Planning meetings
Process Overview
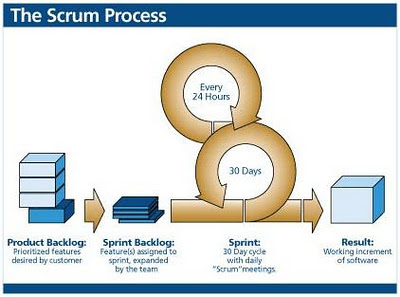
The scrum process has several steps:
1.
The product owner creates of list of requirements, called the Product
Backlog, listed in order of business value.
2.
During a sprint planning meeting, the product owner and team choose the
top items from product backlog that can be completed during a 2 - 4 week
"Sprint" session.
3.
The scrummaster helps the team break down the tasks necessary to
complete the items chosen for the sprint.
4.
During each day of the sprint, a 15-minute meeting is held to discuss
the status of the project - this is the Daily Scrum Meeting
5.
When the sprint is finished, a Sprint Review Meeting is held so the team
can present its work to the product owner, who assesses whether the items are
complete or not, and guides the team as they select the items for their next
sprint.
6.
After the team and scrummaster discuss the failures and successes of the
sprint, the process begins all over again.
Key terms
Scrum - Scrum is an agile project management process that allows you to
deliver usable results during your project
lifecycle, absorbing changes as you
go along.
Product Owner - Establishes and prioritizes the product backlog, or
requirements, based on the interest of all stakeholders and the goals of the
project.
Team - Small team possessing cross-functioning skills that manages and
develops the product or project
ScrumMaster - Helps guide the team through the scrum process, but because the
team is supposed to self-organize, he or she may not necessarily be perceived
as the "leader."
Product Backlog - Documented, prioritized requirements for
the project.
Sprint - 2 - 4 week period where the team works to finish predetermined
deliverables from the product backlog.
Daily Scrum- In a meeting limited to no more than 15 minutes, each team member must
address three items aloud to the rest of the group: what they have done since
yesterday; what they plan to do by tomorrow; and what impediments to progress
they are experiencing.
Sprint Review Meeting - Held at the end of the sprint,
this meeting usually does not exceed a four-hour time limit. The team presents
the part of the project they completed during the sprint to the product owner
and any related stakeholders and establishes which items from the product
backlog they wish to work on next. The team also meets on their own to reflect
upon the performance and performance of the last sprint.
Why It's Useful
Scrum is quickly growing to be one of the most popular project
management techniques for both large and small companies - and for good reason!
The scrum process allows for continual project change and adaptation, innovation,
and self-organization as the team assesses what is working and what's not,
during the sprint. Not only does this flexibility boost team moral and
productivity, it also improves product quality and increases the chances the
company will reach (or exceed) its goals by eliminating and prioritizing
project issues. Scrum also prevents unnecessary product requirements from being
developed because the most valuable items are delivered first.
Reference: http://www.projecttimes.com/articles/rugby-vs-development-what-is-scrum.html